We prioritize system security and customer privacy throughout our engineering process. Every team member undergoes thorough security training and strictly adheres to best practices for data handling, ensuring your data is always protected.
Technology
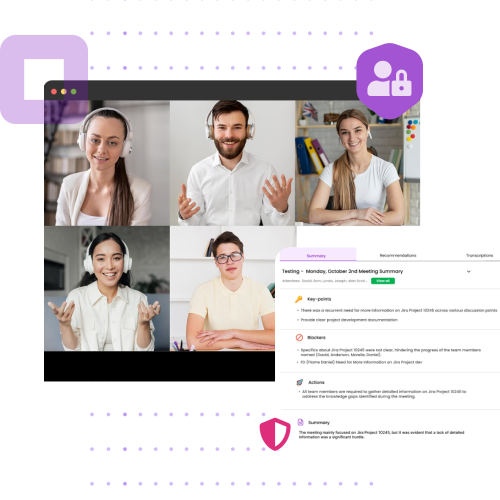
Robust Infrastructure MYPOP is built on robust infrastructure and services that adhere to industry-grade security standards. We encrypt your data at rest, including calendar events and other personally identifiable metadata, ensuring comprehensive protection of your information.

Ico
We adhere to the standards set by the Information Commissioner’s Office (ICO). Our data processing practices meet strict regulatory requirements, safeguarding user information with robust security measures and transparency.

GDPR
MYPOP is fully compliant with the General Data Protection Regulation (GDPR), ensuring user consent in all data processing activities. Our system protects personal data, upholds user rights, and provides clear information on data use. This commitment helps us build and maintain user trust by prioritizing their privacy.
Our Process

Strict controls over data access
We enforce stringent controls over data access using 256-bit AES encryption for storage and 256-bit SSL/TLS encryption for data in transit. Our database is securely hosted in a Virtual Private Cloud with Microsoft Azure, which meets top IT security standards.

Uptime and logging
Our production environments feature security logging and uptime monitoring. This ensures our system's availability and reliability through automated oversight and continuous monitoring.

We implement coding best practices focused on the OWASP Top Ten
We engage third-party security experts to conduct regular penetration tests. Our development, testing, and production environments are separated, and all code changes undergo peer review and rigorous testing before deployment. We follow the best practices outlined in the OWASP Top Ten to maintain robust security.

Uptime and logging
Our production environments have security logging, uptime monitoring, and system availability metrics of our core services. This helps our security team enforce automated monitoring and uptime.

We implement coding best practices focused on the OWASP Top Ten
Development, testing, and production environments are separated. All code changes are peer reviewed and tested prior to deployment into production.
Are you ready to Pop? Meet your AI Agile Copilot
Embark on your AI journey with us! Discover the power of artificial intelligence tailored to your needs.

